How to Create Secret for Default Service account for Kubernetes versions above 1.24
Secrets for ServiceAccounts will no longer be automatically generated by Kubernetes.
What is the change about?
Kubernetes is a powerful container orchestration platform that simplifies the management of complex applications. It offers many features and functionalities that allow you to easily deploy, scale, and manage your applications in a cluster environment. One such feature is the service account, which allows applications running in a Kubernetes cluster to authenticate with the Kubernetes API server and access resources securely.
In earlier versions of Kubernetes, when you create a service account, a secret is automatically created and associated with the service account. This secret contains a token that is used to authenticate the service account with the Kubernetes API server. However, starting from Kubernetes version 1.24, the secret for the service account is no longer created automatically.
Purpose
This behavior change is due to security reasons. Kubernetes is continuously improving its security features to prevent any potential security vulnerabilities. With this change, Kubernetes is making it more secure by requiring the secret to be created manually, thus reducing the possibility of unauthorized access to the API server.
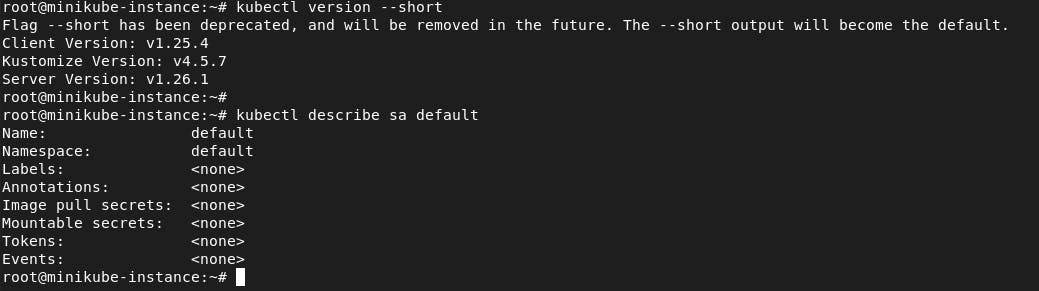
How to Verify
If you're trying to access a secret associated with a service account in Kubernetes, you may find that the secret is not automatically created anymore. To check if a secret exists for a default service account, you can use the command.
kubectl describe sa default
Running the command below command confirms that there is no secret associated with the default service account
Create a Secret for Service Account
To create a secret for a service account, you can use the Kubernetes API or the command-line interface (CLI). You can create the secret by using the below yaml content in secret.yaml file.
apiVersion: v1
kind: Secret
type: kubernetes.io/service-account-token
metadata:
name: access-token
annotations:
kubernetes.io/service-account.name: "default"
Apply this file to create and verify secret using the below commands.
kubectl apply -f secret.yaml
kubectl get secret access-token -o yaml
Summary
In summary, the change in Kubernetes version 1.24 regarding the creation of secrets for service accounts is a positive step towards improving the security of Kubernetes. It ensures that the secrets are created only when needed and by authorized personnel, reducing the risk of unauthorized access to the Kubernetes API server. By manually creating the secret, you have greater control over the secret's lifecycle, making it easier to manage and maintain the security of your Kubernetes cluster.
